- Home
- CFP
- Registration
- Training
- Schedule
- Speakers
- CXO Track
- CTF
- Exhibition
- Live Bug Hunting
- Hack Young
- Resume Clinic
- Media Pass
- Sponsors
- For You
- Venue
- Volunteer
- Nullcon Goa Sep 2022
- Speakers
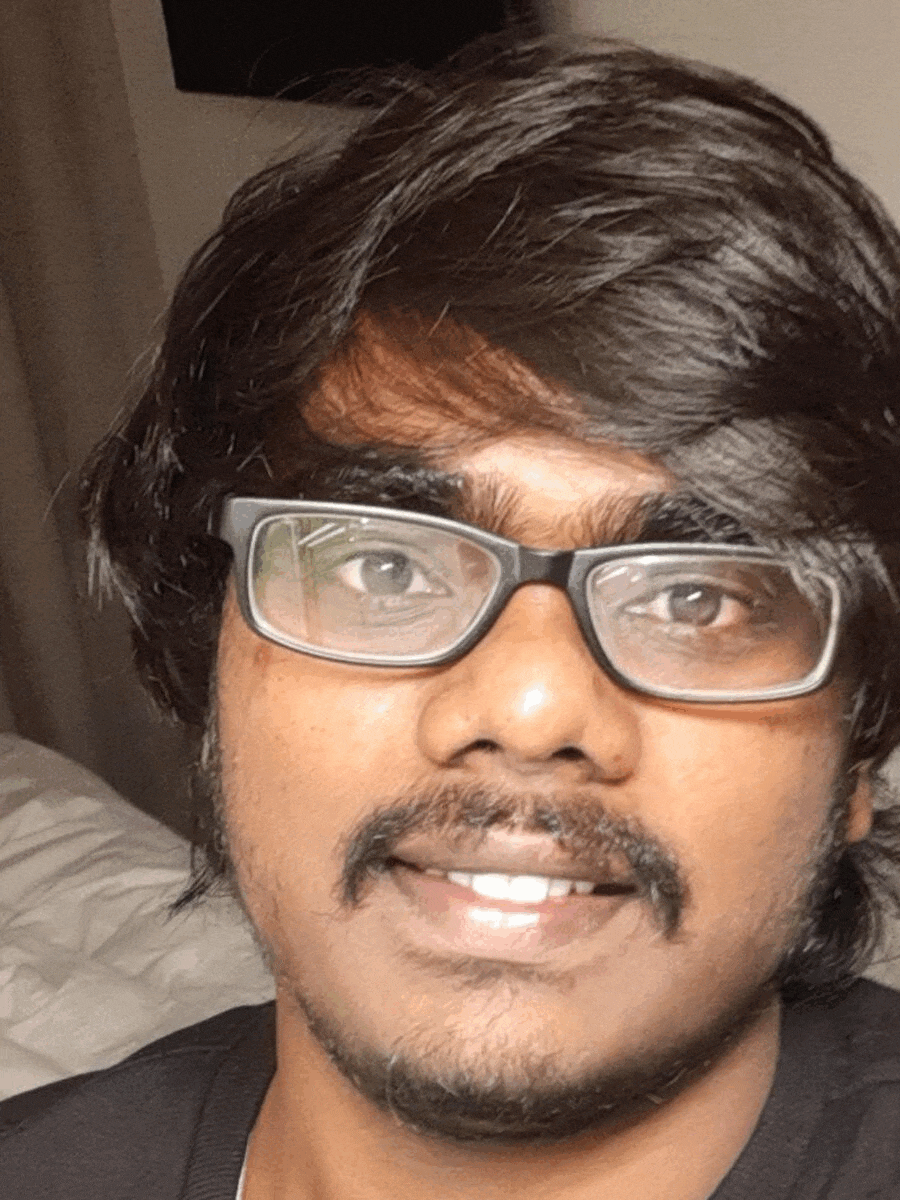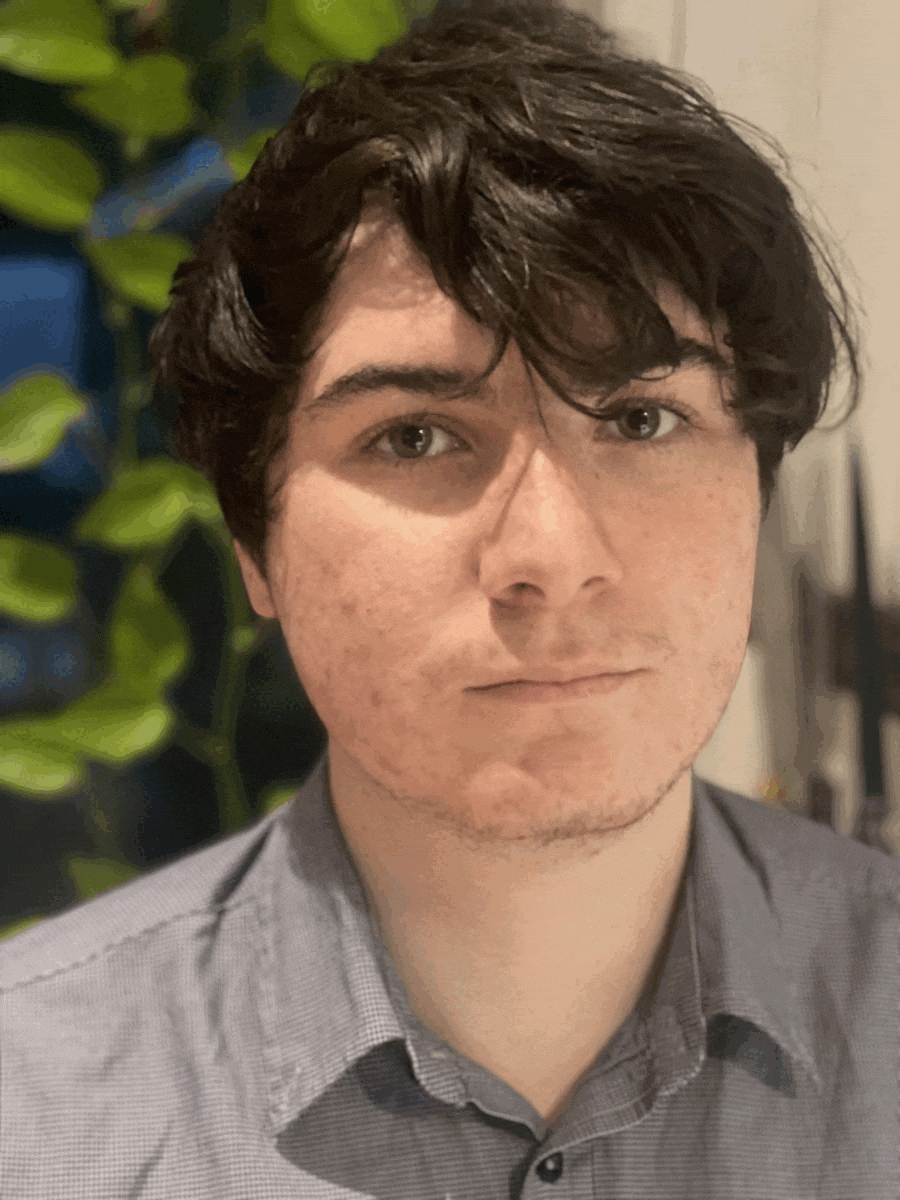
- Mohan Sri Rama Krishna Pedhapati & Maxwell Garrett
Mohan Sri Rama Krishna Pedhapati & Maxwell Garrett
Designation:
Talk Title:
ElectroVolt: Pwning Popular Desktop Apps While Uncovering New Attack Surface On Electron
Abstract:
Electron based apps are becoming a norm these days as it allows encapsulating web applications into a desktop app which is rendered using chromium. However, if Electron apps load remote content of attackers choice either via feature or misconfiguration of Deep Link or Open redirect or XSS it would lead to Remote Code Execution on the OS.
Previously, it was known that lack of certain feature flags and inefficiency to apply best practices would cause this behavior but we have identified novel attack vectors within the core electron framework which could be leveraged to gain remote code execution on Electron apps despite the feature flags being set correctly under certain circumstances. This presentation covers the vulnerabilities found in twenty commonly used Electron applications and demonstrates Remote Code Execution within apps such as Discord, Teams (local file read), VSCode, Basecamp, Mattermost, Element, Notion, and others.
Bio:
Mohan Sri Rama Krishna Pedhapati is an Application Security Auditor at Cure53. Mohan's area of interest is Web and Browser Security. He spends most of his time doing CTFs, security research, and finding vulnerabilities in the wild. He contributes to responsible disclosure programs and is included in the hall of fame for Google, Microsoft, Discord, Steam, and many others. His notable findings/research were finding client-side prototype pollution in the wild which was presented at BSides Ahmedabad, and Cookie tossing vulnerabilities on cloud providers.
Want to connect with Mohan Sri Rama Krishna Pedhapati?
Maxwell Garrett is a 17-year-old Application Security Auditor formerly at Cure53. In his spare time, he also enjoys playing CTF's, doing security research, and playing basketball. Max has found vulnerabilities in Google Chrome, DOMPurify, Outlook Web App and more.
Want to connect with Maxwell Garrett?
Aaditya Purani is a senior security engineer at Tesla. Aaditya's primary areas of expertise are web/mobile application penetration testing, product security reviews, blockchain security, and source code review. He contributes to responsible disclosure programs and is included in the hall of fame for Apple, Google and AT&T. He also participates in capture the flag (CTF) from Perfect Blue which is a globally ranked top-1 CTF team. As a researcher, his most famous public findings include BTCPay Pre-Auth RCE, Brave Browser Vulnerability, and Akamai Zero Trust RCE. As a writer, Aaditya has authored articles for InfoSec Institute, Buzzfeed, Hackin9, and DailyO.
William Bowling is a Senior Software Developer who has been playing CTFs, participating in Bug Bounty Programs, playing underwater hockey, and doing security research in his spare time for over 10 years. Some of his notable findings while performing security research include Arbitrary Code Execution in ExifTool when extracting metadata from a file, and multiple Remote Code execution bugs in both GitLab and GitHub.